Claranet Cyber Security
With 17 years’ experience in cybersecurity services and training, for the...

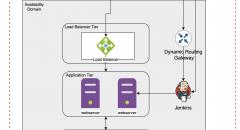
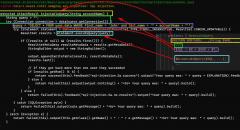
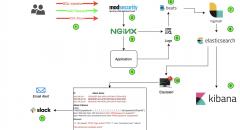
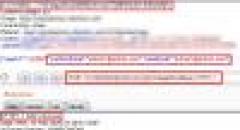
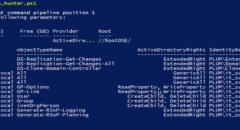
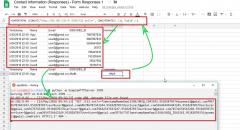
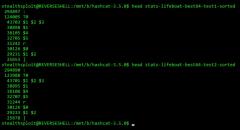
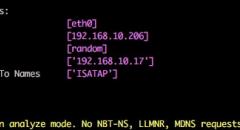
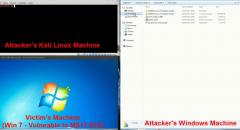
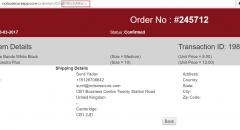
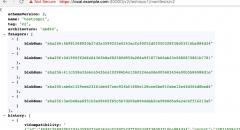
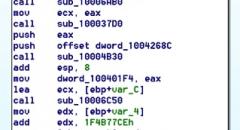
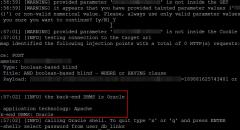
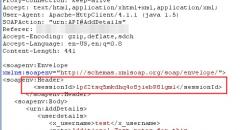
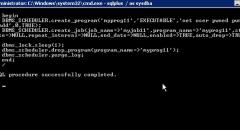
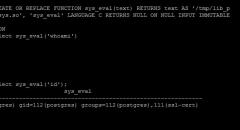
SqliLab CTF, Wrap Up!
As you would have noticed from the noise on twitter and other channels, the...
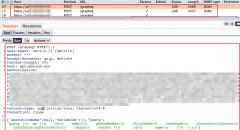
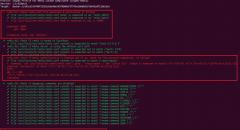
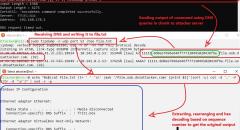
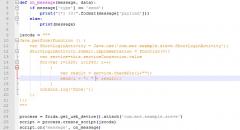
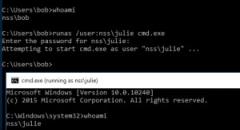
Truecrypt running as sudo
Recently, i was going through the following truecrypt page: https://en....