This past Good Friday, @ShadowBrokers group (https://steemit.com/shadowbrokers/@theshadowbrokers/lost-in-translation) leaked a number of hacking tools/exploits from the NSA’s Arsenal. This leak contained operational notes from the NSA’s actively targeting of banks in the Middle East and their collection of exploitation tools targetting Microsoft Windows systems ranging from XP to Windows 8 and Windows Server 2012.
Link for the release: https://yadi.sk/d/NJqzpqo_3GxZA4
The public exploits for Windows systems are the most concerning, as these could be used to hack into exposed and unpatched Windows systems. In a number of cases these attacks can be performed across the network by targeting SMB, RDP, IMAP, and possibly other protocols. Names have been assigned to these exploits as shown in the figure below:
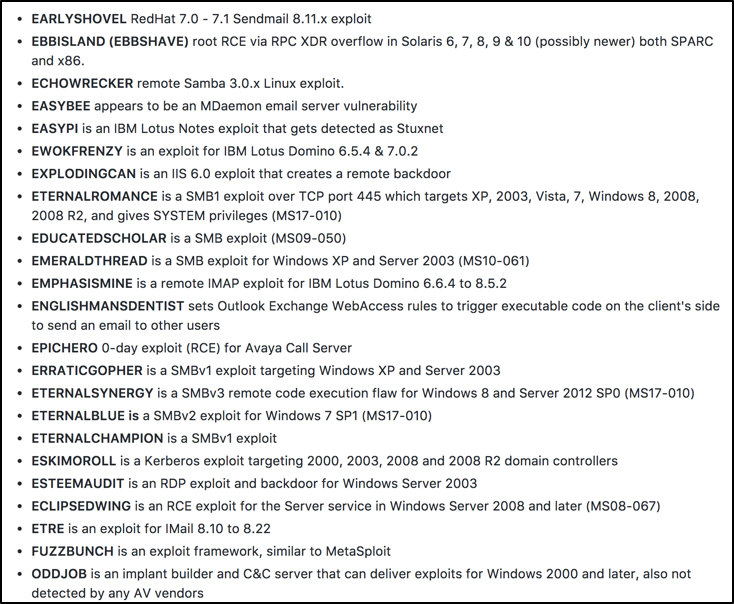 Shadowbroker exploit list
Shadowbroker exploit list
Reference for image: https://github.com/misterch0c/shadowbroker
Microsoft released patches for these exploits last week under the security Advisory MS17-010 https://technet.microsoft.com/en-us/library/security/ms17-010.aspx.
We at NotSoSecure decided to test the functionality of FUZZBUNCH (a very Metasploit-esc interface) in our hacklab and to verify a few of these exploits. @rebootuser tested the ETERNALBLUE exploit and recorded the following video demonstration of the attack against an unpatched Windows 7 host.
ETERNALBLUE is an exploit that targets the SMB protocol and results in RCE if successful. Doublepulsar (seemingly a very powerful) payload was used in this attack, and DLL injection was performed using a DLL generated by msfvenom. As shown in video, successful exploitation returns a Meterpreter session to the attacker’s machine.
As per Microsoft’s blog (https://blogs.technet.microsoft.com/msrc/2017/04/14/protecting-customers-and-evaluating-risk/), patches for all vulnerabilities have been released and thus it is highly recommended that all patches (especially the recent MS17-010) are deployed immediately.
Marketing
For more such vulnerabilities and exploits, check out our Advance Infrastructure Hacking training at Advanced infrastructure hacking