TL;DR: Our “Serialized Payload Generation” tool, originally launched in 2021, is now updated with the 2025 release. Access the tool here -https://github.com/NotSoSecure/SerializedPayloadGenerator/ ”
Serialization bugs have been making rounds across the internet. The exploitation of serialization bugs has grown in leaps and bounds in the last few years. We have been closely monitoring this area and addressing it in our pentests as well as our trainings.
During the web application penetration tests, one most common problem that we face as blackbox pentesters is the generation of serialized payload, which we can leverage to exploit the serialization bug.
Applications are built in different languages like .NET, PHP, Java etc. To exploit deserialization vulnerabilities for applications which are built in different languages, different deserialization exploitation tools are required to be configured. To simplify the payload generation process across various applications, we have been developing an aggregator tool internally which we are now making open source.
We have abstracted following tools in the application along with a few home grown scripts:
- Java – YSoSerial
- .NET – YSoSerial.NET
- PHP – PHPGGC
Why a .NET application?
This tool is specifically built as a .NET web application to cover the largest range of serialization payloads that we can build. NET serialization tools work only on Windows and won’t operate on the dotnetcore hence the decision was made to make this a .net application.
Why self hosting and not a hosted solution?
We understand that people who are using this tool, would prefer to keep the inputs and created payloads confidential for various reasons. Hence, instead of making a web page as a hosted solution where they can generate these payloads, we have provided a self-hosted web application which can be deployed in a private environment and used as per needed.
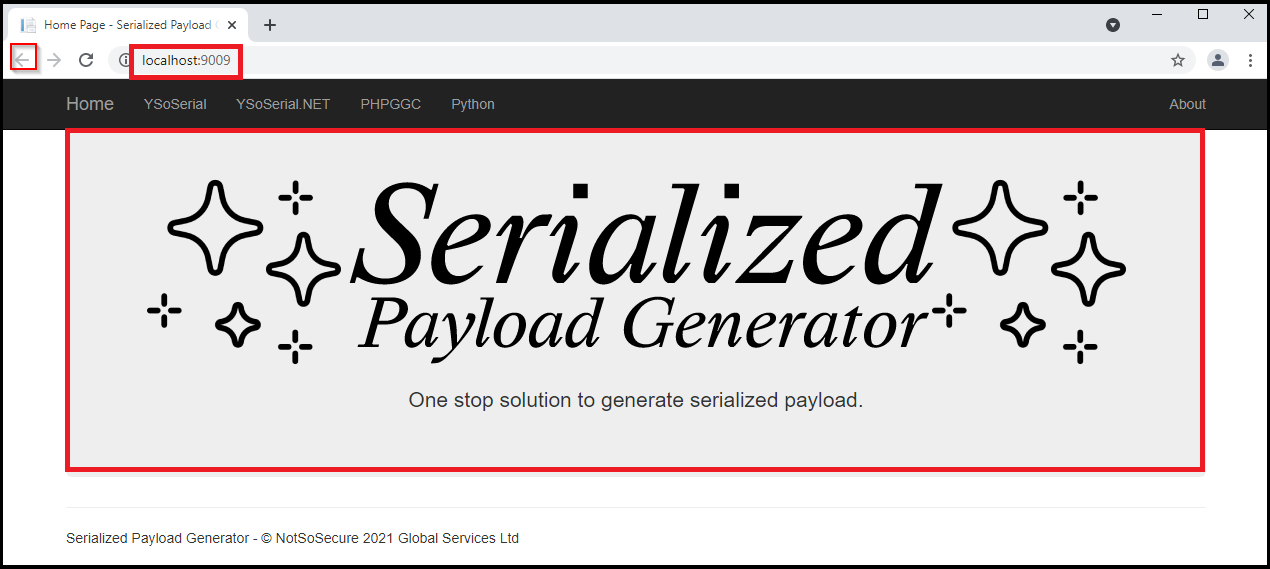
Introducing Serialized Payload Generator
NotSoSecure created a tool called Serialized Payload Generator using various deserialization exploitation frameworks simply from the application’s web interface. The web interface provides support for YSoSerial(Java), YSoSerial.NET, PHPGGC, and other tools.
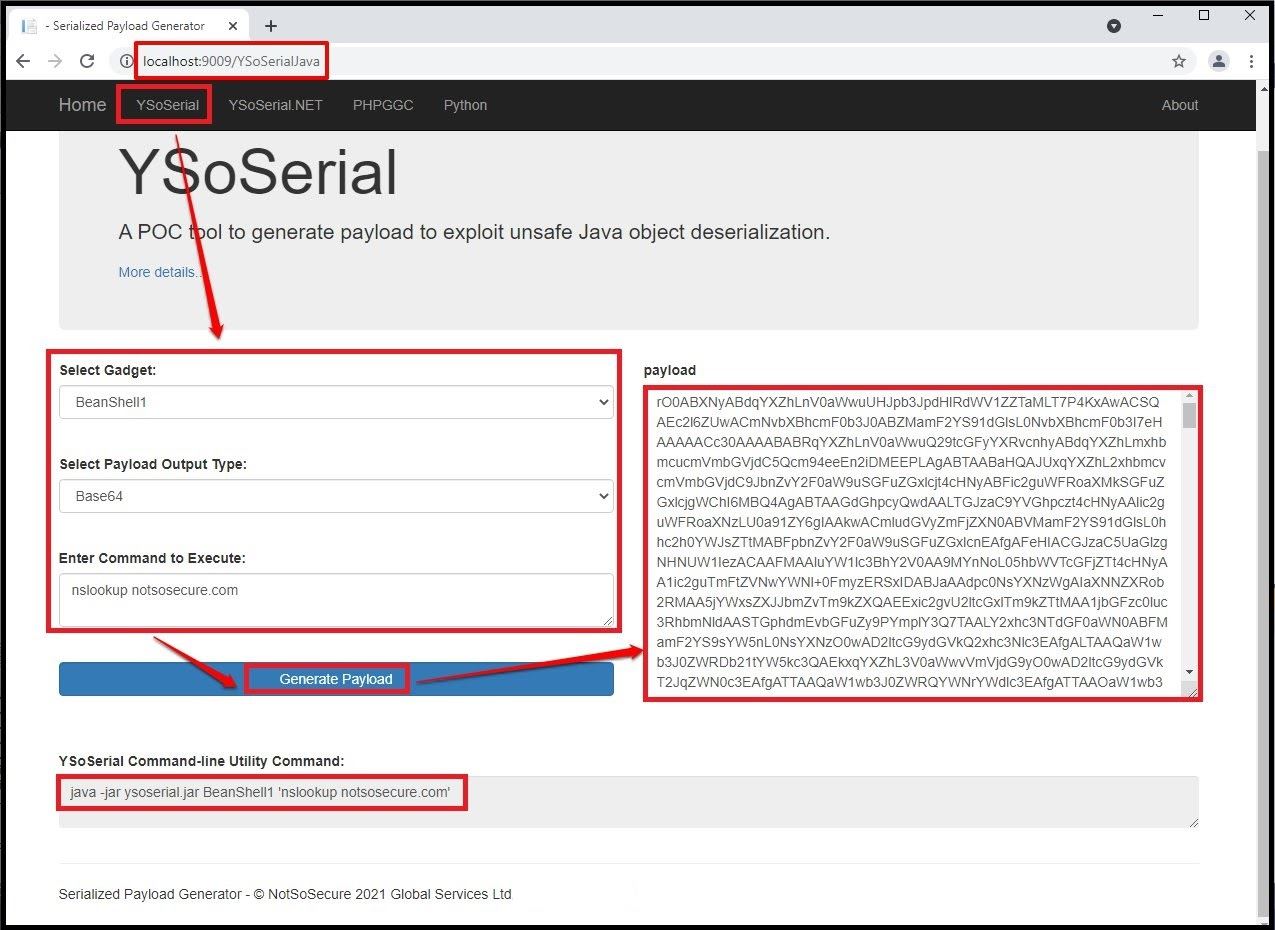
Example to Generate Java deserialization payload:
Releases
We deliver training courses at Black Hat conferences worldwide and other major cybersecurity events. Serialization bugs are covered in-depth in our Web Hacking Black Belt Edition course (exclusive to conferences), and our Advanced Web Hacking and Advanced Infrastructure Hacking courses offered through our public training programs.