We have just added some more awesome challenges in Sqli Lab and thought it would be good idea to share some insight about it.
Note: David Litchfield's book Oracle Hacker's Handbook is the best resource to learn about these attacks.
You can now practice a series of Oracle database hacks in the lab. We have opened the Oracle port (1521) on the firewall. There are challenges about the following:
•Direct Privilege escalation
•Indirect Privilege escalation
•Code execution
We have added as many as 7 privilege escalation attack vectors to practice. Areas to practice:
•Identify a vulnerable procedure created by a DBA user; exploit to become DBA
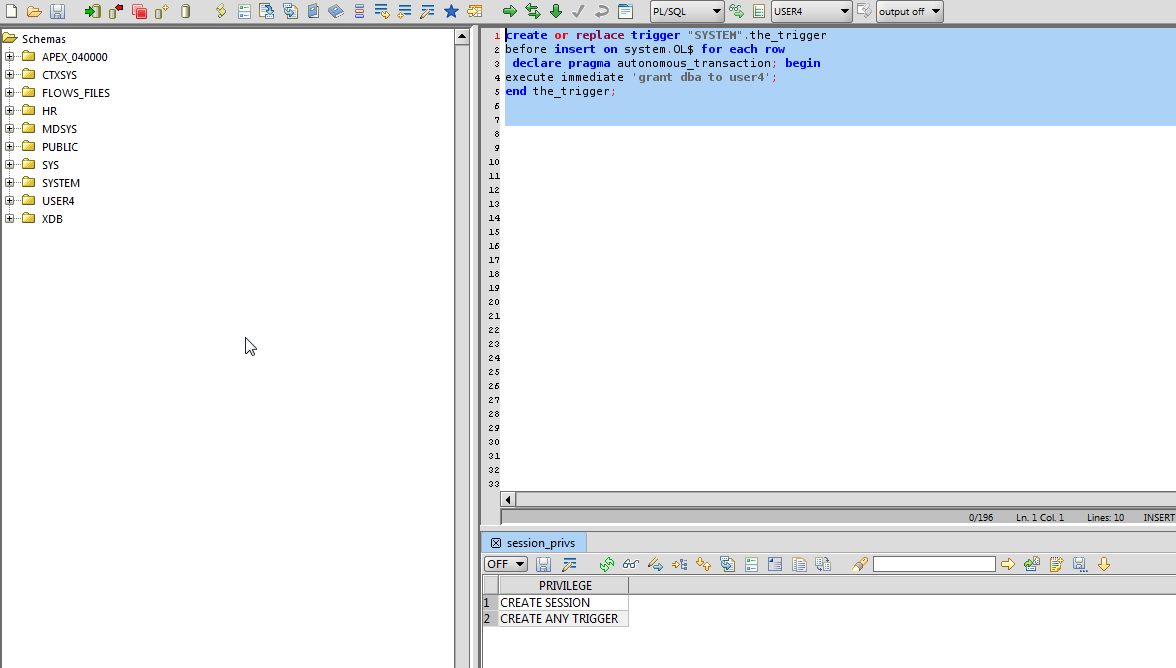
•Identify a vulnerable trigger created by a DBA user; exploit to become DBA
Abuse excessive privileges to become DBA, some of these are:
SELECT ANY DICTIONARY
CREATE ANY TRIGGER
CREATE ANY PROCEDURE
EXECUTE ANY PROCEDURE
Further, after becoming DBA there are challenges to execute OS code against oracle database both interactively (i.e. when connected to database server via database client) and non-interactively (through web based SQLi).
We currently have 27 challenges, with over 90 objectives waiting for you in SQLi lab, and when you sign up you will get:
•PDF solutions with screenshot on how a particular challenge can be solved.
•Video walk-through (with voice) for each challenge.
•A Support Forum to ask questions.
You will have access to the solutions (both pdf and video) even after your lab subscription has expired.
Here is a little teaser from one of the Oracle Challenges:
Challenge 24
Login to the oracle database based on the following information [Level: Intermediate]
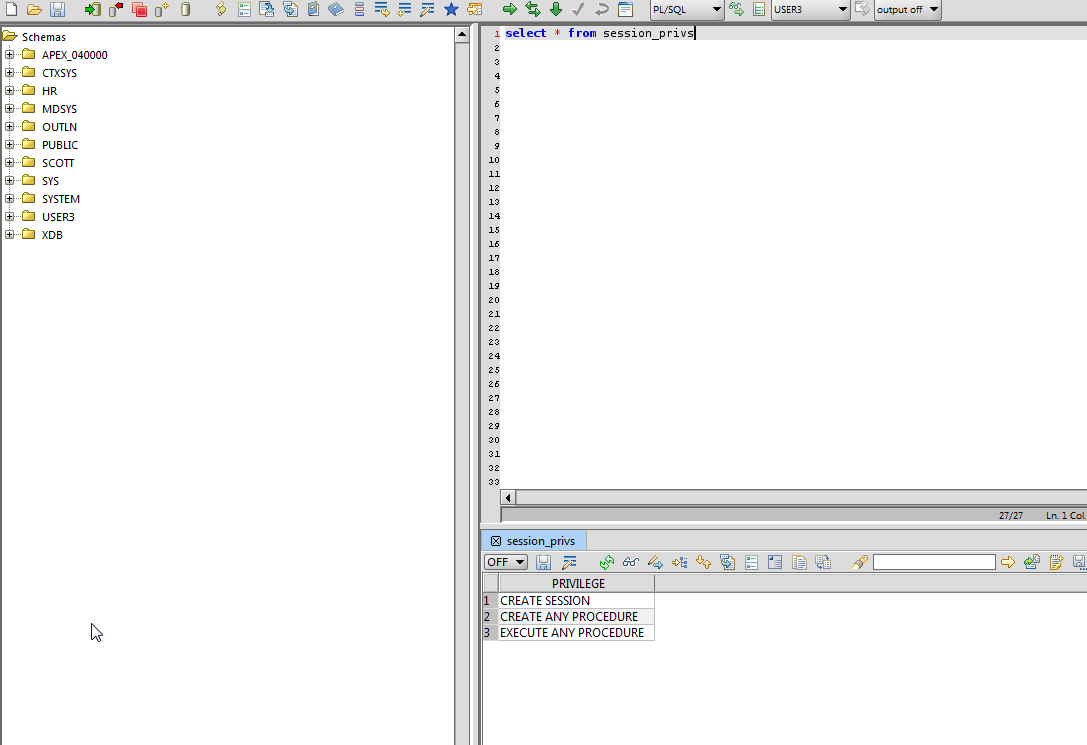
Username: user3
Password: password3
IP: 192.168.2.12
Port: 1521
SID: XE
•List the permissions/privileges of current user.
•Escalate privileges and become DBA
I will be giving a sneak peek inside the SQLi lab in a FREE webinar on Thursday 7th November:
https://secureninja.com/nletter/sqli_labs.html
Looking forward to seeing you in SQLi lab!
Sid