It has been a long time since I posted something. In 2010, I released a paper which talked about how to execute OS code when exploiting a SQL Injection in a web app which talks to oracle database. Back then, I was not aware of 2 publicly available functions which could allow execution of PL/SQL statement. These functions change everything. These functions imply that we can issue multiple statements and overcome the limitations of oracle's SQL language. Interestingly, these 2 functions exist from Oracle 9i upto 11g R2. While I am a little bit puzzled why I didn't see these earlier, I have put together a few attack vectors in a new article/paper titled: Hacking Oracle From Web: Part 2
In a short summary, If you find a SQL Injection in a Oracle web app, you can issue multiple statements by calling one of the two publicly available functions. So, if the injection is in SELECT statement, you can run INSERT, DELETE etc. This also means that if the back-end database has any vulnerability, you can exploit it from the web and get higher privileges. Once you get higher privileges (typically become DBA) then you can execute OS code.
I have also made a small video which shows exploitation of a SQL Injection in an un-patched Oracle database.
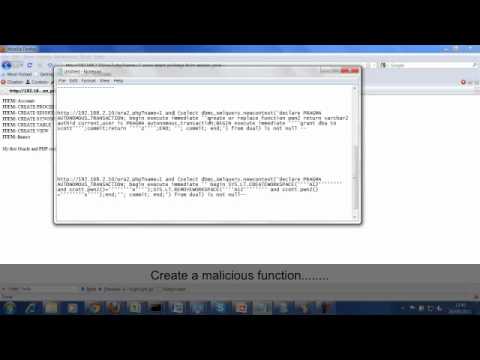
Happy Hacking...