Become a DBA by exploiting the Oracle trigger created by the SYSTEM user? [DB: Oracle, Level: Intermediate]
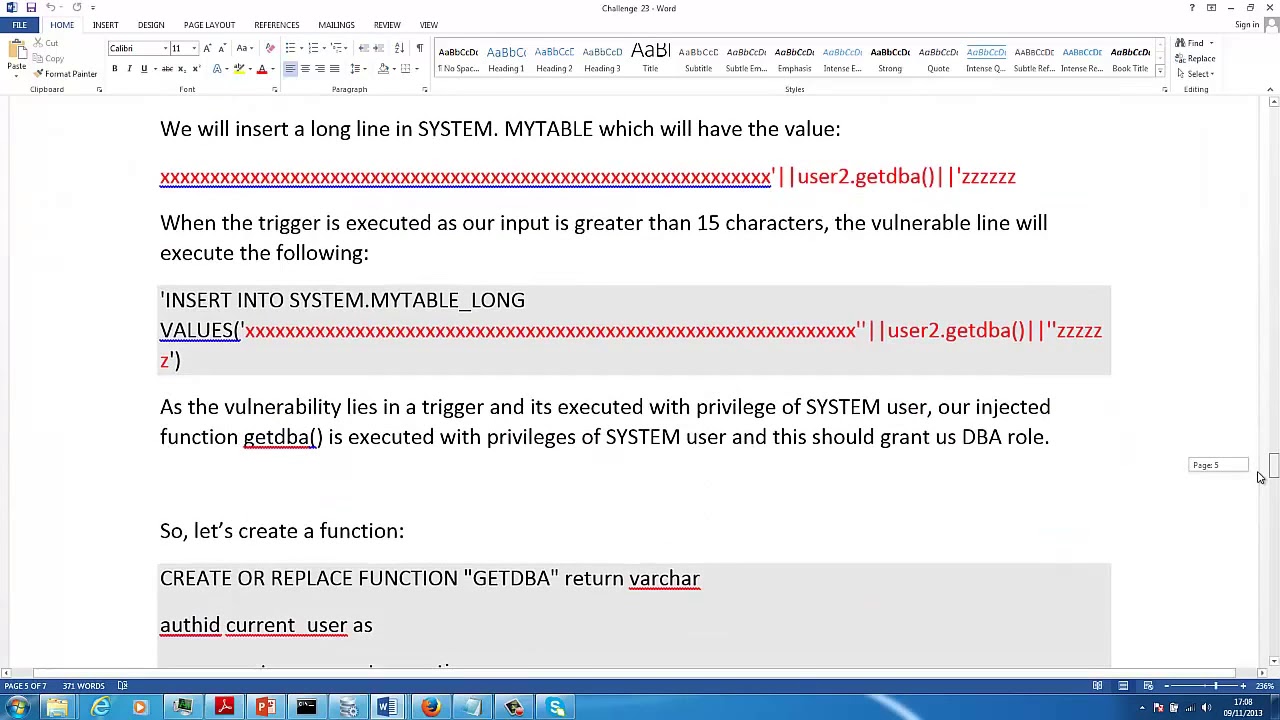
This challenge exemplifies, the steps to exploit a vulnerable trigger created by SYS user to become a privileged DBA user.
Lab: In this lab, we learn how to identify the vulnerable trigger in the Oracle database and dissect the privileges of the current user.
Database: Oracle
Technique Used: Trigger exploitation
Limitations: None
Video Demonstration