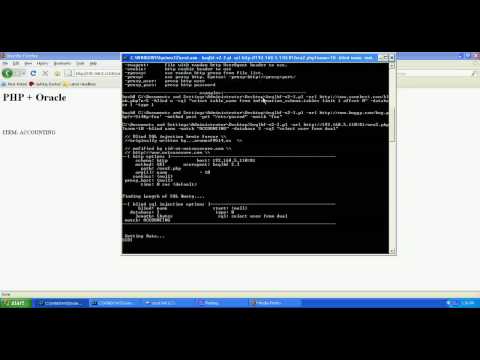
Here is a small video of bsqlbf.
Here we are exploiting a blind SQL Injection in a web app with Oracle back-end. The webapp connects to the database as "scott" (unprivileged) user.
First we run bsqlbf with default parameters and find the user with whose privilege we are executing SQL (scott). Then when we try to read password hashes, the attack fails because the user scott does not have privileges to query sys.user$ table. So, we do privilege escalation with bsqlbf (type 3) and it returns password hash of sys user.
Then we execute O.S command (type 4). In this case, the database server already had a nc.exe in C: drive. We used this to throw us a reverse shell.